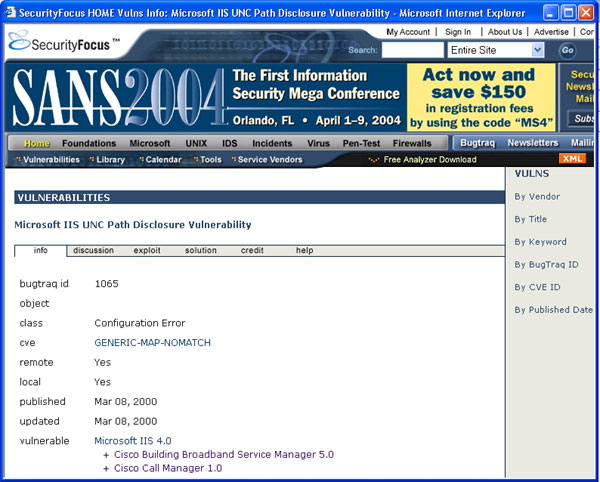
- Detailed information about the signatures is available in three public databases: bugtraq, CVE and arachnids. Click on bugtraq. This would take you to the database, which explains the attack signature, how it is exploited by attackers and the possible solutions to fix it (click on "solution" in the center gray bar).
 will open in a new
window. Please close once viewed.
will open in a new
window. Please close once viewed.